Difference between Virus and Trojan
Key Difference: Viruses are programs or codes that attach themselves to files and programs and run inside the computer without the knowledge of the user. Trojan horse is a non-replicating malware that hides itself as authorized and useful software.
Virus and Trojan are two of many different malwares that are available on the internet. Though virus has become an umbrella term for all different types of malicious software, it differs from Trojan in many ways. Unlike virus, Trojan does not have the ability to self-replicate and must be sent through drive-by downloads. Online users should be aware of the different types of malware that exist and the best way to identify them.
 Viruses are programs or codes that attach themselves to files and programs and run inside the computer without the knowledge of the user. The term ‘virus’ has become an umbrella term for all types of malware, which have the ability to replicate itself and does not include adware and spyware. Viruses have been termed as virus because of their characters that are similar to actual viruses. They can attach to a certain hosts, files and programs and then replicate themselves to completely infect the computer. They can also travel via transference of data and files to infect other systems. All computer viruses are man-made. Almost all viruses are attached to an executable files, which requires the user to run the file in order for the virus to infect the system. There are two types of viruses: Nonresident and Resident. Nonresident viruses, upon execution, immediately start searching for other hosts that can be infected, infect those targets, and finally transfer control to the application program they infected. Resident viruses do not immediately search for hosts and instead loads itself into memory on execution and transfers control to the host program. The main purpose of a virus to infect, alter and damage files. These can also change the name and location of the files and corrupt them to the point that they become unreadable. Computers can be protected by using antivirus and spyware software. In order to remove the virus, infected files can be deleted or the computer can be formatted or restored.
Viruses are programs or codes that attach themselves to files and programs and run inside the computer without the knowledge of the user. The term ‘virus’ has become an umbrella term for all types of malware, which have the ability to replicate itself and does not include adware and spyware. Viruses have been termed as virus because of their characters that are similar to actual viruses. They can attach to a certain hosts, files and programs and then replicate themselves to completely infect the computer. They can also travel via transference of data and files to infect other systems. All computer viruses are man-made. Almost all viruses are attached to an executable files, which requires the user to run the file in order for the virus to infect the system. There are two types of viruses: Nonresident and Resident. Nonresident viruses, upon execution, immediately start searching for other hosts that can be infected, infect those targets, and finally transfer control to the application program they infected. Resident viruses do not immediately search for hosts and instead loads itself into memory on execution and transfers control to the host program. The main purpose of a virus to infect, alter and damage files. These can also change the name and location of the files and corrupt them to the point that they become unreadable. Computers can be protected by using antivirus and spyware software. In order to remove the virus, infected files can be deleted or the computer can be formatted or restored.
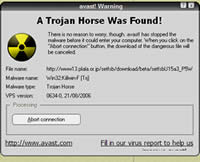 Trojan horse is a non-replicating malware that hides itself as authorized and useful software. It is named after the mythological Trojan horse that allowed the Greeks to win the Trojan War because similar to that Trojan horse, this Trojan also hides under the pretense that it is legitimate software before it is downloaded on to the host system. The user is tricked into thinking that they are downloading authorized and legitimate software such as games, computer files, etc. After it infects a computer it gain full access to the computer, and can attack the system by using popup windows, changing the desktop, adding additional icons to the desktop, etc. It can also be more serious such as deleting files, stealing personal information, activating and spreading other viruses. It can also create a backdoor to the system, allowing hackers easy access to the computer. The Trojan is used for purposes such as use of the machine as part of a botnet, crashing the computer, blue screen of death, electronic money theft, identity theft, keystroke logging, viewing user’s webcam, etc. Computers can be protected using firewalls, anti-virus and spyware software.
Trojan horse is a non-replicating malware that hides itself as authorized and useful software. It is named after the mythological Trojan horse that allowed the Greeks to win the Trojan War because similar to that Trojan horse, this Trojan also hides under the pretense that it is legitimate software before it is downloaded on to the host system. The user is tricked into thinking that they are downloading authorized and legitimate software such as games, computer files, etc. After it infects a computer it gain full access to the computer, and can attack the system by using popup windows, changing the desktop, adding additional icons to the desktop, etc. It can also be more serious such as deleting files, stealing personal information, activating and spreading other viruses. It can also create a backdoor to the system, allowing hackers easy access to the computer. The Trojan is used for purposes such as use of the machine as part of a botnet, crashing the computer, blue screen of death, electronic money theft, identity theft, keystroke logging, viewing user’s webcam, etc. Computers can be protected using firewalls, anti-virus and spyware software.
Trojans and viruses are dangerous viruses as they can be used to infect the computer with other malicious software. Trojans can be installed using worms, which allows a Trojan to run on the computer. These malicious software allows hackers to view a person’s personal details as well as take over complete control of the computer. It is best to protect the computer using firewalls, using anti-virus and spyware software. Experts also advice that users should not download or access files that seem suspicious.
|
|
Virus |
Trojan |
|
Definition |
A virus is a program code that attaches itself to a program or file and infects other computers through that file. |
Trojan is a non-replicating malware that hides itself as authorized and useful software. |
|
Controlled remotely |
No |
Yes |
|
Process of infection |
Attaches itself to an executable file, folder or program. |
It presents itself as a non-harming software before it damages the system. |
|
Process of spreading |
Viruses rely on transfer of files or other programs in order to spread to other systems. |
It does not replicate. It must be downloaded as a software and executed. |
|
Infecting files |
Yes, it modifies, alters or deletes certain files. |
It does not modify files, it steels the users’ information and harms the host computer. |
|
Speed of spreading |
Faster compared to Trojan. |
Very slow. |
|
Type |
Malware |
Malware |
|
Replication |
Yes |
No |
|
Protection |
Antivirus software |
Antivirus software |
|
Removal |
Antivirus, formatting, system restore. |
Antivirus, formatting, system restore. |
Image Courtesy: security.arizona.edu, cloudsafe365.com








Add new comment